The Devices which is used in computer for connecting with network is called Computer Network. Networking hardware includes all computers, Peripherals, Interface cards and other Equipment needed to perform data-processing and communications within the network.
This section provides information on the following components:
2. Workstations
3. Network Interface Cards
4. Switches
5. Repeaters
6. Bridges
7. Routers
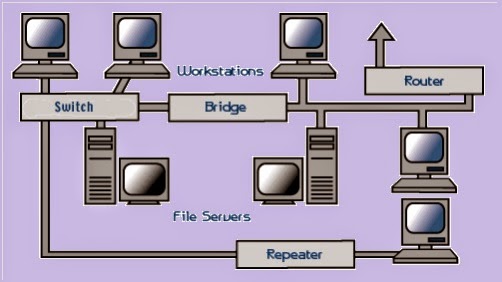
File Servers: A file server stands at the heart of most networks. It is a very fast computer with a large amount of RAM and storage space, along with a fast network interface card. The network operating system software resides on this computer, along with any software applications and data files that need to be shared. The file server controls the communication of information between the nodes on a network. For example, it may be asked to send a word processor program to one workstation, receive a database file from another workstation, and store an e-mail message during the same time period. This requires a computer that can store a lot of information and share it very quickly. File servers should have at least the following characteristics:
• 800 megahertz or faster microprocessor (Pentium 3 or 4, G4 or G5)
• A fast hard drive with at least 120 gigabytes of storage
• A RAID (Redundant Array of Inexpensive Disks) to preserve data after a disk casualty
• A tape back-up unit (i.e. DAT, JAZ, Zip, or CD-RW drive)
• Numerous expansion slots
• Fast network interface card
• At least 512 MB of RAM
Workstations: The entire user computers connected to a network is called workstations. A typical workstation is a computer that is configured with a network interface card, networking software, and the appropriate cables. Workstations do not necessarily need floppy disk drives because files can be saved on the file server. Almost any computer can serve as a network workstation.
Network Interface Cards: The network interface card (NIC) provides the physical connection between the network and the computer workstation. Most NICs are internal, with the card fitting into an expansion slot inside the computer. Some computers, such as Mac Classics, use external boxes which are attached to a serial port or a SCSI port. Laptop computers can now be purchased with a network interface card built-in or with network cards that slip into a PCMCIA slot. Network interface cards are a major factor in determining the speed and performance of a network. It is a good idea to use the fastest network card available for the type of workstation you are using. The three most common network interface connections are Ethernet cards, Local Talk connectors, and Token Ring cards. According to a International Data Corporation study, Ethernet is the most popular, followed by Token Ring and Local Talk.
Ethernet Cards: Ethernet cards are usually purchased separately from a computer, although many computers (such as the Macintosh) now include an option for a pre-installed Ethernet card. Ethernet cards contain connections for either coaxial or twisted pair cables (or both) . If it is designed for coaxial cable, the connection will be BNC. If it is designed for twisted pair, it will have a RJ-45 connection. Some Ethernet cards also contain an AUI connector. This can be used to attach coaxial, twisted pair, or fiber optics cable to an Ethernet card. When this method is used there is always an external transceiver attached to the workstation
Local Talk Connectors: Local Talk is Apple’s built-in solution for networking Macintosh computers. It utilizes a special adapter box and a cable that plugs into the printer port of a Macintosh. A major disadvantage of Local Talk is that it is slow in comparison to Ethernet. Most Ethernet connections operate at 10 Mbps (Megabits per second). In contrast, Local Talk operates at only 230 Kbps.
Token Ring Cards: Token Ring network cards look similar to Ethernet cards. One visible difference is the type of connector on the back end of the card. Token Ring cards generally have a nine pin DIN type connector to attach the card to the network cable.
Switch: A concentrator is a device that provides a central connection point for cables from workstations, servers, and peripherals. In a star topology, twisted-pair wire is run from each workstation to a central switch/hub. Most switches are active, that is they electrically amplify the signal as it moves from one device to another. Switches no longer broadcast network packets as hubs did in the past, they memorize addressing of computers and send the information to the correct location directly. Switches are usually configured with 8, 12, or 24 RJ-45 ports ,Often use end in a star or star-wired ring topology, Sold with specialized software for port management ,Also called hubs ,usually installed in a standardized metal rack that also may store net-modem, bridges, or routers.
Repeaters: Since a signal loses strength as it passes along a cable, it is often necessary to boost the signal with a device called a repeater. The repeater electrically amplifies the signal it receives and rebroadcasts it. Repeaters can be separate devices or they can be incorporated into a concentrator. They are used when the total length of your network cable exceeds the standards set for the type of cable being used. A good example of the use of repeaters would be in a local area network using a star topology with unshielded twisted-pair cabling. The length limit for unshielded twisted-pair cable is 100 meters. The most common configuration is for each workstation to be connected by twisted-pair cable to a multi-port active concentrator. It’s amplifies all the signals that pass through it allowing for the total length of cable on the network to exceed the 100 meter limit.
Bridges: A bridge is a device that allows you to segment a large network into two smaller, more efficient networks. If you are adding to an older wiring scheme and want the new network to be up-to-date, a bridge can connect the two. A bridge monitors the information traffic on both sides of the network so that it can pass packets of information to the correct location. Most bridges can “listen” to the network and automatically figure out the address of each computer on both sides of the bridge. The bridge can inspect each message and, if necessary, broadcast it on the other side of the network. The bridge manages the traffic to maintain optimum performance on both sides of the network. You might say that the bridge is like a traffic cop at a busy intersection during rush hour. It keeps information flowing on both sides of the network, but it does not allow unnecessary traffic through. Bridges can be used to connect different types of cabling, or physical typologies. They must, however, be used between networks with the same protocol.
Routers: A router translates information from one network to another; it is similar to a super-intelligent bridge. Routers select the best path to route a message, based on the destination address and origin. The router can direct traffic to prevent head-on collisions, and is smart enough to know when to direct traffic along back roads and shortcuts. While bridges know the addresses of all computers on each side of the network, routers know the addresses of computers, bridges, and other routers on the network. Routers can even “listen” to the entire network to determine which sections are busiest — they can then redirect data around those sections until they clear up. Routers can direct signal traffic efficiently, route messages between any two protocols, route messages between linear bus, star, star-wired ring topologies, route messages across fiber optic, coaxial and twisted-pair cabling .
I hope this will surely help you. If you have any questions or problem let me know. Please Comment on Below.
I hope this will surely help you. If you have any questions or problem let me know. Please Comment on Below.
If you like this Post Share with Your friends on Facebook ,Twitter Google+ or have a some suggestion about this post comment Below






![[Top 10] Best ways to Earn Money Online 2023 popular ways to earn online money](https://bytizenotes.com/wp-content/uploads/2023/02/make-money-online-100x70.png)